In today’s digital world, your company’s reputation can be destroyed in seconds. A single data breach doesn’t just expose sensitive information—it shatters customer trust, damages your brand image, and can cost millions in lost revenue. Recent studies reveal that 58% of consumers believe brands hit by a data breach are untrustworthy, and a staggering 70% would stop shopping with a brand that suffered a security incident.
But here’s the good news: implementing robust data loss prevention software can not only prevent these disasters but also help rebuild trust when incidents occur. This comprehensive guide will show you exactly how data loss prevention solutions protect your brand’s most valuable asset—your reputation.
Understanding the Real Cost of a Data Breach
Before we dive into solutions, let’s understand what’s truly at stake. The impact of a data breach extends far beyond immediate financial losses.
Financial Damage
The numbers are sobering. According to recent industry data, the average cost of a data breach reached $4.44 million globally in 2025. However, in the United States, this figure skyrocketed to an all-time high of $10.22 million per breach. These costs include regulatory fines, legal fees, notification expenses, and remediation efforts.
But the financial bleeding doesn’t stop there. Companies often see their stock prices plummet following a breach announcement. Research shows that publicly traded companies experience an average drop of 7.5% in stock values, translating to an average loss of $5.4 billion in market capitalization. It typically takes these companies 46 days just to recover their stock prices to pre-breach levels.
Reputation and Trust Erosion
The intangible costs are even more devastating. When customers lose faith in your ability to protect their data, they take their business elsewhere. Studies demonstrate that 65% of data breach victims lose trust in an organization following a breach, while 80% of consumers in developed countries will completely abandon a business if their personal information is compromised.
Even more concerning, 86% of consumers stated they were unlikely to do business with an organization that had suffered a breach involving credit or debit card details. This trust deficit creates a long-term reputation problem that’s far harder to fix than any technical security issue.
What is Data Loss Prevention and Why Does It Matter?
Defining Data Loss Prevention Software
Data Loss Prevention (DLP) is a comprehensive cybersecurity approach that protects sensitive company information from both external attacks and internal threats. What is data loss prevention? Simply put, it’s a set of technologies, processes, and policies designed to ensure that confidential data doesn’t leave your organization through unauthorized channels.
Modern DLP solutions work by monitoring, detecting, and blocking sensitive data from being transferred, shared, or accessed inappropriately. These systems classify information in real-time, enforce security policies automatically, and alert cybersecurity teams to potential violations before they become full-blown disasters.
The Three Pillars of Data Protection
Effective data loss prevention software addresses data in three critical states:
Data at Rest refers to information stored in databases, file systems, cloud repositories, or backup storage. This includes customer records, financial documents, intellectual property, and employee information sitting on servers or in the cloud.
Data in Motion encompasses information being transmitted across networks—whether sent via email, uploaded to cloud services, transferred to USB drives, or shared through messaging apps. This is where many breaches occur, as data moving between systems is particularly vulnerable.
Data in Use involves information actively being accessed or processed by applications and users. This includes data in RAM, CPU registers, or being actively edited in documents. Monitoring data in use helps identify suspicious activity patterns that might indicate a security threat.
How Data Loss Prevention Software Protects Your Brand
Proactive Threat Prevention
The best defense against reputation damage is preventing breaches before they happen. Top data loss prevention software solutions provide multiple layers of protection that work together to stop threats at every stage.
Advanced DLP systems continuously monitor user behavior to identify unusual patterns that might signal a security risk. For instance, if an employee who normally accesses 50 files per day suddenly attempts to download 5,000 files, the system flags this as suspicious activity and can automatically block the action while alerting security personnel.
Real-time content inspection scans all data transfers, whether via email, cloud uploads, or external devices. If someone attempts to send a document containing credit card numbers, social security numbers, or proprietary business information through an unsecured channel, the DLP software stops the transfer immediately.
Insider Threat Detection
Not all security risks come from external hackers. In fact, insider threats—whether malicious or accidental—account for a significant portion of data breaches. A recent survey found that approximately 30% of large businesses and 25% of small businesses have encountered insider threats and data leaks.
Data loss prevention solutions excel at identifying insider risks through behavioral analytics. These systems establish baseline patterns for each user and detect deviations that might indicate data theft, corporate espionage, or simple negligence. This includes monitoring activities like:
- Unusual file access patterns or attempting to access restricted information
- Copying large volumes of data to personal devices or cloud storage
- Printing sensitive documents outside normal work hours
- Attempting to disable security software or circumvent monitoring systems
- Accessing confidential files shortly before resignation
By catching these behaviors early, DLP software prevents reputation-damaging incidents before data ever leaves your organization.
Compliance and Regulatory Protection
In today’s regulatory environment, data protection isn’t optional—it’s the law. Regulations like GDPR, HIPAA, SOC 2, and dozens of other frameworks mandate specific security controls for handling sensitive information. Non-compliance doesn’t just result in fines; it destroys customer confidence.
Data loss prevention software helps organizations maintain compliance by automatically enforcing regulatory requirements. The system can identify which data falls under which regulations, apply appropriate security controls, generate compliance reports, and maintain detailed audit trails.
For example, healthcare organizations handling patient data must comply with HIPAA regulations. A robust DLP solution automatically identifies Protected Health Information (PHI), restricts access to authorized personnel only, encrypts data in transit and at rest, logs all access attempts for audit purposes, and blocks unauthorized sharing attempts.
This automated compliance enforcement not only prevents violations but also demonstrates to customers, partners, and regulators that your organization takes data protection seriously.
Rapid Incident Response and Damage Control
Despite best efforts, breaches can still occur. When they do, the speed and effectiveness of your response directly impacts the damage to your reputation. Organizations that detect and contain breaches quickly suffer significantly less reputational harm than those with prolonged detection times.
Current data shows that the average time to identify and contain a breach fell to 241 days in 2025—a nine-year low, but still far too long. Companies using advanced DLP solutions typically identify incidents in a fraction of that time, with some detecting anomalies within hours or even minutes.
When a DLP system detects a potential breach, it immediately initiates automated response protocols. This includes blocking the suspicious activity to prevent further data exfiltration, alerting security teams with detailed context about the incident, isolating affected systems to contain the breach, preserving forensic evidence for investigation, and generating incident reports for stakeholders.
This rapid response capability minimizes the volume of data exposed and demonstrates to customers and regulators that your organization has robust security measures in place. In fact, research shows that when internal security teams identify breaches first before third parties or attackers, the average cost of the breach is $4.18 million compared to $5.08 million when attackers disclose it.
Key Features of Effective Data Loss Prevention Software
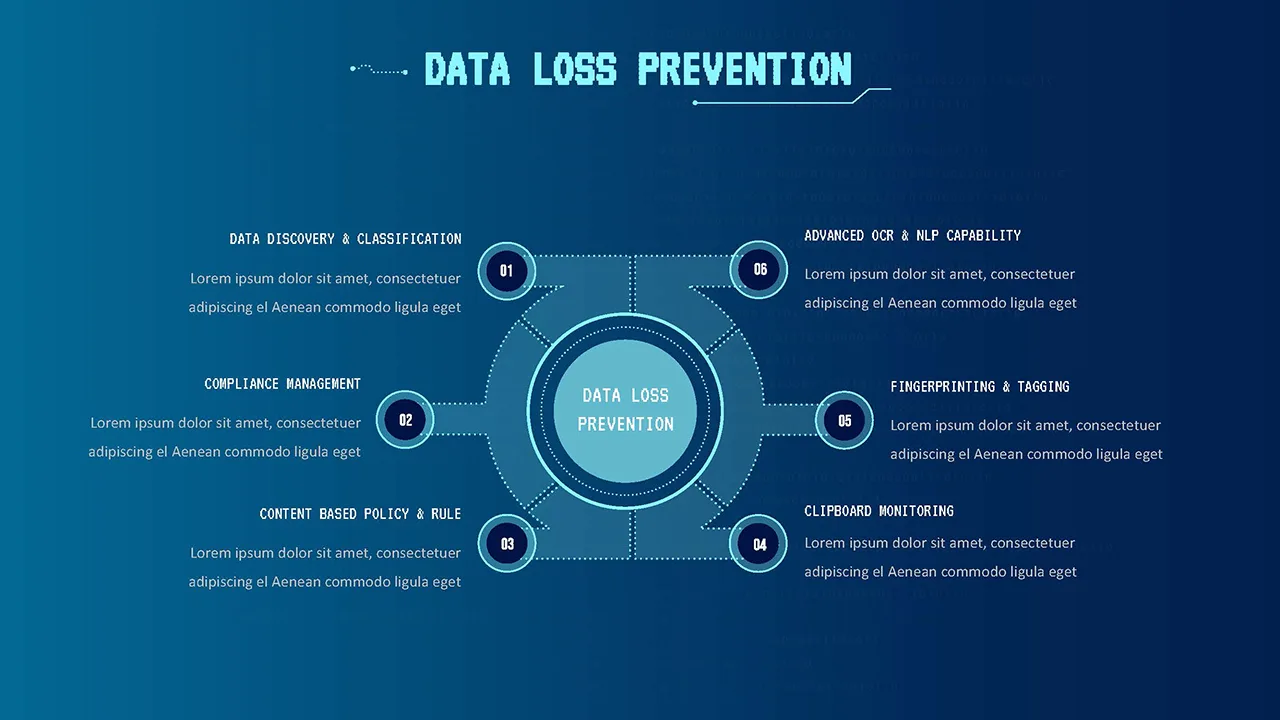
Content Discovery and Classification
You can’t protect what you don’t know you have. Comprehensive DLP solutions start with data discovery—automatically scanning your entire IT environment to identify where sensitive information resides. This includes on-premise servers, cloud storage, endpoint devices, email archives, and backup systems.
Once discovered, the software classifies data based on sensitivity levels. This might include public information with no security restrictions, internal data requiring basic protection, confidential information with strict access controls, and highly sensitive data requiring maximum security.
Advanced systems use multiple classification methods including content-based analysis that scans files for sensitive patterns like credit card numbers or social security numbers, context-based classification that evaluates metadata such as file location, creator, or application, and user-based classification where employees manually tag sensitive documents.
This comprehensive visibility ensures nothing falls through the cracks and every piece of sensitive data receives appropriate protection.
User Activity Monitoring and Behavioral Analytics
Understanding how users interact with data is crucial for identifying threats. Modern DLP solutions employ sophisticated behavioral analytics to establish normal usage patterns and detect anomalies.
These systems track a wide range of activities including application usage and website visits, file access, copying, and transfer operations, print jobs and screenshot captures, clipboard operations, email and messaging communications, and external device connections.
By analyzing these patterns over time, the software develops user behavior baselines and can instantly recognize when someone deviates from their normal routine. This approach catches both malicious insiders trying to steal data and well-meaning employees inadvertently creating security risks.
Policy Enforcement and Automated Controls
Creating security policies is one thing; enforcing them consistently across thousands of users and millions of files is another challenge entirely. Data loss prevention software automates policy enforcement, ensuring that security rules apply uniformly without requiring constant manual oversight.
Organizations can define granular policies based on data type, user role, department, location, time of day, destination, and risk level. When a policy violation is detected, the system can take immediate action such as blocking the activity entirely, requiring additional authentication, encrypting the data automatically, removing sensitive content from messages, alerting security personnel, or logging the incident for review.
This automated enforcement removes the human error factor and ensures consistent protection even as your organization grows.
Integration and Scalability
Data loss prevention doesn’t work in isolation. The most effective solutions integrate seamlessly with your existing security infrastructure including email gateways, web proxies, endpoint protection platforms, SIEM systems, identity and access management tools, and cloud access security brokers.
This integration creates a unified security ecosystem where different tools share threat intelligence and coordinate responses. For example, if your DLP system detects a compromised user account, it can automatically trigger your identity management system to disable that account across all platforms.
Scalability is equally important. As your organization grows, your DLP solution should expand effortlessly to protect new users, devices, and data repositories without requiring extensive reconfiguration.
Real-World Impact: How DLP Saves Reputations
Preventing Customer Data Exposure
Consider a financial services company handling thousands of customer transactions daily. Without proper protection, a single employee mistake—like sending an unencrypted spreadsheet containing account numbers to the wrong recipient—could expose thousands of customers to fraud risk.
With data loss prevention software in place, the system would automatically detect that the email contains sensitive financial information, block the transmission before it leaves the company network, alert the employee and their supervisor, provide secure alternatives for sharing the information, and log the incident for training purposes.
The customer never knows how close their data came to being compromised, and the company’s reputation remains intact.
Stopping Intellectual Property Theft
A technology company spent years developing a proprietary algorithm that gives them a competitive advantage. A disgruntled employee with access to this information decides to share it with a competitor before leaving the company.
An effective DLP system would detect when the employee accesses files they don’t normally use, identify attempts to copy sensitive technical documents, block transfers to personal email accounts or cloud storage, alert security teams to the suspicious pattern, and preserve evidence of the attempted theft.
The intellectual property stays secure, the competitive advantage is maintained, and the company’s market position and reputation remain strong.
Managing Third-Party Risks
Modern businesses often share data with partners, contractors, and vendors. Each connection point represents a potential vulnerability. Over 80% of companies that operate in the financial sector have 1,500 or more sensitive files visible to all employees, creating enormous risk exposure.
Data loss prevention software manages these risks by controlling what data external parties can access, monitoring all third-party data transfers, automatically encrypting shared information, revoking access when contracts end, and maintaining audit trails of all external data sharing.
This controlled approach to data sharing allows businesses to collaborate effectively while maintaining security and protecting their reputation.
Building a Culture of Data Protection
Employee Training and Awareness
Technology alone can’t protect your reputation—you need people who understand why data security matters. Approximately 60% of employees have brought data from their previous workplace to their current employer, often without realizing they’re creating security and legal risks.
Effective data protection requires comprehensive employee education covering the types of threats facing the organization, common attack vectors like phishing and social engineering, secure data handling practices, how to recognize and report suspicious activity, and the business and reputational impacts of data breaches.
Many modern DLP solutions include training capabilities that provide real-time feedback when employees violate policies. Instead of just blocking an action, the system explains why it was blocked and suggests the correct approach. This turns every policy enforcement into a teachable moment.
Leadership Commitment and Resource Allocation
Data protection requires investment—not just in technology, but in people, processes, and ongoing maintenance. Organizations where leadership actively champions security initiatives see significantly better outcomes than those where security is treated as a check-box exercise.
This commitment must include adequate budget for security tools and staff, regular security assessments and updates, involvement in policy development, accountability for security outcomes, and open communication about security priorities.
When employees see that leadership takes data protection seriously, they’re far more likely to follow security protocols themselves.
Continuous Improvement and Adaptation
The threat landscape evolves constantly, with attackers developing new techniques and targeting new vulnerabilities. Your data loss prevention strategy must evolve accordingly.
This requires regular review and updating of security policies, analysis of blocked attempts and near-misses, integration of threat intelligence from industry sources, testing of incident response procedures, and evaluation of new security technologies.
Organizations that treat security as a journey rather than a destination maintain stronger defenses and better protect their reputations over the long term.
Choosing the Right Data Loss Prevention Solution
Essential Capabilities to Look For
Not all DLP solutions are created equal. When evaluating options, prioritize systems that offer comprehensive data discovery across all environments including on-premise, cloud, and endpoints, support for all three data states including at rest, in motion, and in use, advanced threat detection using behavioral analytics and machine learning, flexible deployment options such as cloud, on-premise, or hybrid, and integration capabilities with existing security infrastructure.
Additionally, consider the solution’s scalability to grow with your organization, ease of management with intuitive interfaces and automation, comprehensive reporting for compliance and analysis, and responsive technical support when issues arise.
Deployment Considerations
The right deployment model depends on your organization’s specific needs, infrastructure, and resources. Cloud-based solutions offer rapid deployment, minimal maintenance, automatic updates, and flexible scaling. They’re ideal for organizations without extensive IT security teams or those with distributed workforces.
On-premise solutions provide complete control over data, integration with legacy systems, customization options, and may be required for certain regulatory environments. Many organizations choose hybrid deployments that combine the control of on-premise solutions with the flexibility of cloud services.
Cost-Benefit Analysis
While data loss prevention solutions require investment, the cost is modest compared to the potential losses from a breach. Consider that the average data breach costs $4.44 million globally and $10.22 million in the United States, while 70% of consumers would stop shopping with a breached brand, and regulatory fines can reach millions of dollars.
Many DLP solutions offer pricing that scales with your organization, making enterprise-grade protection accessible even to smaller businesses. When evaluating costs, factor in not just the software licensing but also implementation services, training and education, ongoing maintenance and support, and integration with existing systems.
Even a modest investment in data loss prevention delivers substantial ROI when it prevents a single significant breach.
The Future of Data Protection and Brand Reputation
Emerging Trends in Data Security
The data security landscape continues to evolve rapidly. Several trends are shaping the future of data loss prevention including AI and machine learning that enhance threat detection and reduce false positives, zero trust architectures that assume no user or system is trustworthy by default, cloud-native security designed for modern cloud-first infrastructure, privacy-enhancing technologies that protect data while maintaining usability, and automated response capabilities that contain threats faster than any human could.
Additionally, 16% of all breaches in 2025 involved attackers using AI, demonstrating that both defenders and attackers are leveraging advanced technologies. Organizations that embrace these innovations will maintain stronger security postures and better protect their reputations.
The Growing Importance of Transparency
Modern consumers are more privacy-conscious than ever. They want to know how their data is being used, how it’s being protected, and what happens if something goes wrong. Organizations that embrace transparency around their security practices build stronger customer relationships.
This includes clearly communicating what data you collect and why, how you protect that information, what security measures are in place, how you respond to incidents, and your commitment to ongoing security improvement.
Data loss prevention software supports this transparency by providing detailed documentation of security controls, audit trails demonstrating compliance, incident reports showing rapid response, and metrics proving the effectiveness of security measures.
Proactive vs. Reactive Security
The most successful organizations have shifted from reactive security—responding after breaches occur—to proactive protection that prevents incidents before they happen. This mindset shift recognizes that reputation damage is far easier to prevent than to repair.
Proactive security includes continuous monitoring and threat hunting, regular security assessments and penetration testing, staying current with emerging threats and vulnerabilities, updating policies and controls based on new risks, and investing in employee security awareness.
Data loss prevention software is a cornerstone of this proactive approach, providing the visibility, controls, and automation needed to stop threats before they impact your business.
Taking Action: Implementing Data Loss Prevention Today
Getting Started with Data Loss Prevention
If your organization hasn’t implemented comprehensive data loss prevention, now is the time to start. The process typically involves several key steps.
First, conduct a data inventory to understand what sensitive information you have and where it resides. This assessment should cover all systems, applications, and storage locations across your entire IT environment.
Next, assess your current risks by identifying potential vulnerabilities in your existing security controls, evaluating insider threat scenarios, reviewing third-party data sharing practices, and analyzing compliance requirements for your industry.
Define your security policies based on this assessment, establishing clear rules for data handling, access controls, acceptable use guidelines, incident response procedures, and compliance requirements.
Finally, select and implement appropriate data loss prevention software that matches your needs, infrastructure, and budget. Start with a pilot program in high-risk areas before rolling out enterprise-wide.
Measuring Success and ROI
Once implemented, measure your DLP program’s effectiveness through various metrics including number of policy violations detected and prevented, reduction in data exposure incidents, time to detect and respond to threats, compliance audit results, and employee security awareness improvements.
These metrics not only demonstrate ROI to leadership but also identify areas for ongoing improvement. Remember that a significant number of detected violations often indicates your system is working—it’s finding and stopping threats that previously went unnoticed.
Building Long-Term Resilience
Data loss prevention isn’t a one-time project; it’s an ongoing commitment to protecting your organization’s data, reputation, and customer trust. Success requires continuous monitoring and refinement, regular training and awareness programs, staying current with evolving threats, adapting to new technologies and business models, and maintaining leadership support and resource commitment.
Organizations that embrace this long-term perspective build resilient security programs that not only protect against current threats but adapt to future challenges.
Conclusion: Your Reputation is Worth Protecting
In today’s digital economy, your brand’s reputation is inseparable from your ability to protect customer data. A single breach can undo years of trust-building and cost millions in lost revenue, regulatory fines, and remediation expenses. The statistics are clear: 58% of consumers consider breached brands untrustworthy, 70% would stop doing business with a breached organization, and the average breach costs over $4 million.
But you’re not powerless against these threats. Implementing robust data loss prevention software provides the protection, visibility, and control needed to safeguard sensitive information and maintain customer trust. From preventing insider threats to ensuring regulatory compliance, from detecting anomalies in real-time to responding rapidly when incidents occur, modern DLP solutions offer comprehensive protection that goes far beyond simple file blocking.
The question isn’t whether you can afford to implement data loss prevention—it’s whether you can afford not to. Every day without comprehensive protection is another day your organization’s reputation hangs in the balance. Whether you choose a solution focused on endpoint monitoring, network security, cloud protection, or comprehensive coverage across all environments, the important thing is to act now.
Your customers trust you with their most sensitive information. Your employees depend on your organization’s stability. Your stakeholders expect responsible data stewardship. Data loss prevention software is how you honor those expectations and protect what matters most—your reputation.
Don’t wait for a breach to prove the value of data protection. Implement comprehensive data loss prevention today and ensure your brand’s reputation remains intact tomorrow and for years to come. The investment you make in security today will pay dividends in customer trust, regulatory compliance, and peace of mind for years to come.
Remember, in the digital age, your reputation is only as strong as your weakest security control. Make data loss prevention a priority, and protect the trust that took years to build.